TSCM 101
A series on technical surveillance countermeasures.

The Future of TSCM
In an age of rising corporate espionage and digital threats, understanding Technical Surveillance Countermeasures (TSCM) is essential. Discover how technologies like AI and IoT are transforming TSCM into proactive protection strategies. Explore the vital role of human expertise alongside advanced tools, and learn how TSCM is crucial for governments, corporations, and private clients. Join us as we examine the future of TSCM and its importance in safeguarding privacy.

TSCM vs. Cyber
In 2025, the threats to your organization are evolving—data breaches and corporate espionage are no longer isolated incidents. While cybersecurity protects your digital assets, TSCM (Technical Surveillance Countermeasures) secures your physical environment from hidden surveillance devices. Together, they form a comprehensive defense strategy against both tangible and intangible threats. Discover the key differences between TSCM and cybersecurity, how they work in tandem, and why integrating both is essential for safeguarding your sensitive information. Don’t leave your organization vulnerable; learn how to fortify your defenses today!
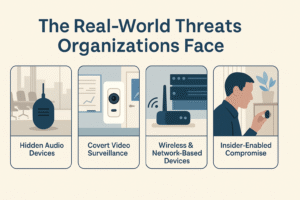
The Real-World Threats Organizations Face
Most people believe that surveillance only occurs in spy movies. However, in reality, the most prevalent surveillance threats arise in everyday workplaces, meeting rooms, and even vehicles. If your organization discusses strategy, finances, or sensitive information, someone might be eavesdropping. From hidden audio devices to covert video surveillance, these dangers are genuine and often remain unnoticed. Uncover the four primary categories of surveillance risks and understand why Technical Surveillance Countermeasures (TSCM) are vital for safeguarding your organization. This isn’t paranoia; it’s contemporary security. Continue reading to learn how to effectively protect your sensitive information.
Common Myths About “Bug Sweeps”
When organizations hear the phrase “bug sweep,” they often picture Hollywood-style scenes of security experts waving high-tech devices. However, this creates dangerous misconceptions. Technical Surveillance Countermeasures (TSCM) are a critical, methodical security discipline, and believing in myths can leave you exposed to real threats. In our latest article, we debunk the five most common myths about bug sweeps, revealing the truth behind this essential security practice. Discover why a one-time sweep isn’t enough and learn how to protect your sensitive information effectively. Don’t let misconceptions compromise your security—read on to find out what you really need to know!

What TSCM Is (and Isn’t)?
Technical Surveillance Countermeasures (TSCM) is more than just a “bug sweep.” In this article, we break down what TSCM really is—and what it isn’t—so organizations can understand how professional sweeps protect sensitive conversations and information.
