Persistent Monitoring Solution
The CastNet Solution
Traditional TSCM sweeps provide point-in-time protection. But today’s surveillance threats evolve between visits — devices can be planted, activated, or disguised in hours.
CastNet’s Persistent Monitoring Solution fills the gap with a discreet, continuous threat detection system that provides real-time awareness of hidden surveillance signals, unauthorized transmissions, and anomaly indicators.
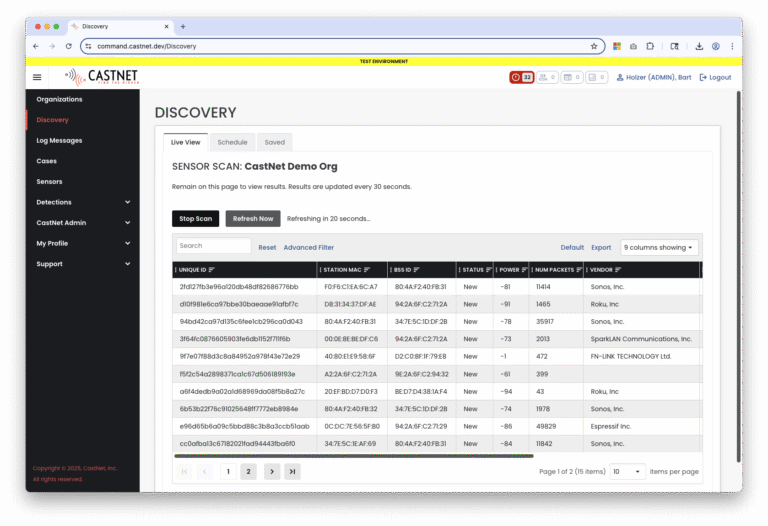
CastNet implements this solution with a Sensor installed at the monitored location and a cloud-based Command Center for oversight of devices at multiple locations.
Sensor
One or more Sensors are installed at the monitored location to scan the local airwaves – WiFi & Bluetooth in our current model. Sensors can also receive feeds from network taps or switch span ports for additional network coverage.
Sensors can monitor authorized, unauthorized, and adjacent WiFi networks.

A Sensor makes contact with the Command Center via WiFi or hardwired network Internet connection. This connection is a SASE connection (think: modern VPN), providing a secure connection with end-to-end encryption.
Command Center
Cloud-hosted software communicates with Sensors to provide command and control, receive data, perform updates, and execute tasks.
CastNet developers created the Command Center using modern DevSecOps, including the concepts of Secure-by-Design and Secure-by-Default.
How It Works
CastNet has developed a proprietary, patent-pending technology for detecting hidden cameras. Actually, the technology can be used to detect any number of suspicious, unauthorized, or rogue devices!
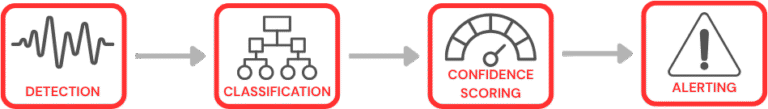
Detection
The first step is Detection – the initial identification of a new device. All devices are considered Unknown when first seen, then attempts to Classify the device are made.
Classification
The second step is Classification – attempting to determine exactly what a device is. A device may have a number of properties and purposes, so this is where our secret recipe enters the mix.
Confidence Scoring
As Classifications are made, a confidence level is assigned. The highest score is considered the most likely way to classify a device.
Alerting
Want to be alerted when hidden cameras and drones are identified? We can do that! We currently alert based on email, text messages, and in-app (in the Command Center) notifications. Notification preferences are specific to each user.
What else can it do!?!
The Persistent Monitoring Solution was initially developed to find hidden cameras. But, what if you are concerned about other types of devices, such as drones? Monitoring the network traffic and airwaves around a location provides our technology incredible insights into activity at the monitored location. Our system can detect:
- Known Devices – Need to track a disgruntled employee? We can alert you to when that person’s phone returns to the property. Or, we can provide attendance metrics for current employees based on their phone presence.
- Drones – We can alert you if signals related to drone operation are detected in your area.
- Increased presence of people – sometimes referred to as the “party detector,” this detection method can identify anomalies in the number of people present at a site. This could indicate an unauthorized party at a rental property or a mob gathering outside a corporate headquarters.
